IPSec tunneling
Order Instructions:
The example used in class was a company merger between a large corporate building in Chicago and a large corporate building in San Diego. By describing the path from one user in Chicago, how does a packet make it to San Diego using IPSec?
SAMPLE ANSWER
Table of Contents
3.1 IPSec Authentication Header (AH) 4
3.2 Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE) 5
4.0 IPSec authentication using IPv4 versus IPv6. 5
5.2 IPSec Network topology: Packet from Chicago to San Diego. 8
5.3 Layer Two Tunneling Protocol (L2TP) over IPSec. 9
IPSec Tunneling
1.0 IPSec Overview
The Internet Protocol Security (IPSec) provides Layer three security (RFC 2401). It is a collection of algorithms, services, and protocols that are utilized in securing IP data at the network layer. It provides a complete security solution for an IP network. The services and protocols of the IPSec combine to offer different kinds of protection. Given that the IPSec works at the IP layer, it is able to offer these protections for higher-layer TCP/IP applications or protocols with no need for extra security methods (Somesh, 2011). The protection services that the IPSec offers are as follows: it authenticates the integrity of a message so that the message is not altered en route; it encrypts user data to ensure privacy; and it protects against some kinds of security attacks for instance replay attacks. Other kinds of protection services are: the capability of devices to negotiate the security keys and algorithms that are needed to satisfy their security needs; and 2 security modes – transport and tunnel – to satisfy the various network needs (Somesh, 2011). IPSec combines various constituents: internet key exchange (IKE), authentication headers (AH), security associations (SA), and encapsulating security payload (ESP).
2.0 IPSec Standards
Given that IPSec is in fact a set of protocols and techniques, it is not described in just one internet standard. The services, architecture, as well specific protocols that are utilized in IPSec are defined by a set of Request for Comments (RFCs). There are a number of Internet Protocol Security Standards as illustrated in the table below:
| RFC Number | Name | Description | |
| 1 | RFC 2402 | IP Authentication Header (AH) | This defines the IPSec AH protocol utilized for ensuring origin verification and integrity of data |
| 2 | RFC 2401 | Security Architecture for IP | This is the key Internet Protocol Security document. It describes the architecture as well as the operation of the technology. It also illustrates how various parts fit together (Kozierok, 2012). |
| 3 | RFC 2403 | The use of HMAC-MD5-96 in AH and ESP | Defines a certain encryption algorithm for use by the ESP and AH protocols known as Message Digest 5 or MD5, HMAC variant. |
| 4 | RFC 2406 | IP ESP | Defines the IPSec Encapsulating Security Payload protocol that provides encryption of data for confidentiality (Somesh, 2011) |
| 5 | RFC 2404 | The use of HMAC-SHA-1-96 in AH and ESP | Defines a certain encryption algorithm for use by ESP and AH known as Secure Hash Algorithm 1 (SHA-1), HMAC variant |
| 6 | RFC 2409 | The IKE | Defines the Internet Key Exchange protocol which is utilized in negotiating security associations and exchanging keys between different devices for secure communications. |
| 7 | RFC 2408 | Internet Security Association and Key Management Protocol (ISAKMP) | Describes the techniques used to exchange keys and negotiate security associations |
| 8 | RFC 2412 | The OAKLEY Key Determination Protocol | Defines a generic protocol for key exchange (Kozierok, 2012) |
The IPSec technology is mostly used to implement virtual private networks (VPNs)
3.0 IPSec Architecture
3.1 IPSec Authentication Header (AH)
This offers authentication services for Internet Protocol Security. AH enables the recipient of a message to confirm that the hypothetical originator of the message was in fact the one who sent that message. Moreover, the AH enables the recipient of a message to confirm that intermediate devices have not altered any of the data within the datagram. In addition, it offers protection against reply attacks, a situation in which an authorized user captures a message and then resends it (Somesh, 2011).
3.2 Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE)
ESP encrypts the payload of the Internet Protocol datagram. It encrypts the data and secures it against eavesdropping during transit (Knight, 2010). IKE is a protocol negotiation as well as key exchange protocol, which enables the communicating parties to negotiate the techniques of secure communication. The IPSec offers security in 3 situations: gateway-to-gateway; host-to-gateway; and host-to-host. The IPSec operates in 2 modes: tunnel mode for virtual private network (VPN), and transport mode for end-to-end (Knight, 2010).
4.0 IPSec authentication using IPv4 versus IPv6
4.1 IPv6
In IPv6, the Authentication Header protects nearly all of the IPv6 base header, the authentication header itself, the IP payload, as well as the non-mutable extension headers after the authentication header (Dominik & Yvette, 2011). Protection for the IPv6 header does not include the mutable fields.
4.2 IPv4
In an IPv4 datagram, Knight (2010) stated that the Protocol field shows the identity of the UDP or TCP that is carried in the datagram. This field therefore points to the next header at the front of the IP payload. In IPv4 the Authentication Header protects the IP payload as well as every header field of an IP datagram with the exception of mutable field – those which may be in transit –, and the IP options like the IP Security Option RFC 1108 (Knight, 2010).
5.0 IPSec tunneling
5.1 IPSec Tunnel Mode
IPSec could be configured to operate in either the Transport mode or the Tunnel mode; Tunnel mode is the default mode. When the IPSec is configured to operate in the Tunnel mode, the whole IP packet will be protected by IPSec; the IPSec will wrap the original packet, encrypt that packet, add a new IP header, and then send it to the other side of the Virtual Private Network tunnel (Dominik & Yvette, 2011). It is notable that Tunnel Mode is mainly utilized between gateways – ASA firewalls or Cisco routers. It is also commonly utilized at an end-station to a gateway; the gateway will act as a proxy for the hosts behind it. Tunnel mode is used in encrypting traffic between secure IPSec Gateways, for instance 2 Cisco routers that are connected over the internet through IPSec Virtual Private Network (Dominik & Yvette, 2011).
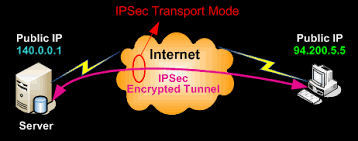
An IPSec tunnel between an IPSec Gateway and a Cisco VPN Client is an example of tunnel mode. The client will connect to the IPSec Gateway. Traffic from client is encrypted, encapsulated within a new IP packet and is then transmitted to the other end. Once a firewall appliance decrypts it, the original IP packet of the client is sent to the local network. An IPSec header – ESP header or AH header – in the tunnel mode is inserted between the upper layer protocol and the IP header. Between ESP and AH, ESP is most widely utilized in IPSec virtual private network configuration (Somesh, 2011).The figure below shows IPSec Tunnel mode with an ESP header:
The figure below shows IPSec Tunnel mode with an AH header:
When IPSec is in the tunnel mode, the AH could be applied together with the ESP or it could be applied alone. The function of the AH is to protect the whole packet (Hoffman, 2011). It is notable that the AH does not protect each field in the New IP Header since some change while in transit, and the sender is not able to envisage the way they may change. In essence, the AH will protect everything that does not change while in transit (Hoffman, 2011).
5.2 IPSec Network topology: Packet from Chicago to San Diego
Path of the packet from Chicago to San Diego
The IPSec network topology above illustrates how a packet moves from Site A in Chicago to Site B in San Diego. VPN is a secure and inexpensive technique for site-to-site connectivity such as the one illustrated above (Hoffman, 2011). Each site runs VPN servers. With IPSec Virtual Private Networks, offices in the two different locations can be connected together over the internet with the strong encryption as well as security that the IPSec protocol offers. In this topology, IPSec offers secure communication in the path through which the packet moves through from the sender in Chicago to the destination in San Diego.
5.3 Layer Two Tunneling Protocol (L2TP) over IPSec
L2TP is basically an industry-standard internet tunneling protocol which offers encapsulation for the sending of Point-to-Point (PPP) frames through packet-oriented media. Layer 2 Tunneling Protocol enables IP traffic to be encrypted before being sent via any medium which supports PPP datagram delivery, for instance IP (Hoffman, 2011). The Microsoft implementation of the Layer 2 Tunneling Protocol makes use of IPSec encryption in protecting data stream from the Virtual Private Network client to the VPN server.
Tunneling, as Knight (2010) pointed out, is the whole process of encapsulation, routing, as well as decapsulation. The tunneling process encapsulates or wraps the original packet within a new packet, which may have new routing and addressing information that allows it to move through a network. When data confidentiality is combined with tunneling, then the original packet data in addition to the original source and destination, is not made known to those who listen to traffic on the network (Hoffman, 2011). The encapsulation is removed the moment the encapsulated packet gets to its destination, and the original packet header is utilized in routing the packet to its last destination, which in this case is San Diego. It is notable that the tunnel is the logical data path wherein the packets that have been encapsulated travel through. To the original source as well as destination peer, this particular tunnel is transparent and it appears similar to another PPP connection within the network path. The peers are not aware of any routers, proxy servers, switches, or other security gateways between the starting point and the endpoint of the tunnel (Hoffman, 2011). Tunneling can be utilized in providing a Virtual Private Network when it is combined with confidentiality.
In the figure shown above, the packets that have been encapsulated travel through the network within the IPSec encrypted tunnel. The internet is the network. The gateway is an edge gateway which stands between the private network and the outside network. Carmouche (2009) pointed out that the edge gateways could normally be a proxy server, a firewall, a router, or any other security gateway. Moreover, two gateways could be utilized within the private network for the purpose of protecting traffic across untrusted sections of the network. Whenever the IPSec is utilized in tunnel mode, Carmouche (2009) stated that the IPSec itself offers encapsulation only for the IP traffic. IPSec tunnel mode is utilized mainly for interoperability with other gateways, routers, or end systems which do not support Layer 2 Tunneling Protocol over IPSec (Carmouche, 2009).
6.0 References
Carmouche, J. H. (2009). Basic IPSec VPN Topologies and Configurations. Columbus, OH: CRC Press.
Dominik, S., & Yvette E., G. (2011). Securing IP Multimedia Subsystem with the appropriate Security Gateway and IPSec Tunneling. 보안공학연구논문지, (3), 385.
Hoffman, P. (2011). Cryptographic Suites for IPSec. Crescent City, CA: Penguin Publishers.
Knight, P. (2010). Dynamic Routing Inside IPSec VPNs. Nortel Networks.
Kozierok, C. (2012). TCP/IP Guide: IPSec Authentication Header. Boston, MA: Penguin Publishers.
Somesh, J. (2011). IP, IPSec, and Related RFCs. Albany, NY: CRC Press.
We can write this or a similar paper for you! Simply fill the order form!




