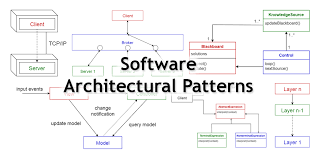
Software Architecture
Order Instructions:
Problem Description (Refined version of Assignment 4):
You’re developing the software for a company that monitors home alarm systems. After reviewing some of the your outline of patterns you would use, our customer that you create a couple diagrams of what you architecture looks like using the notations described in our book “Software Architectures in Practice” and that you apply the techniques described in Chapter 14 to analyze your architecture to verify that the architecture will satisfy the requirement of the system. The have provided a revised description (next paragraph), with some more details.
There will be one sensor for each door or window in the home that detects when they are opened. If the home alarm system is activated, the home (sub)system must (1) turn on the alarm within 5 seconds of sensing the opening of any opening other than a door next to a control pad, which allow 30 for the user disarm code to be entered before the alarm is turned on, and (2) send an alarm to the Alarm Monitor Company’s central monitoring location within 15 seconds for an opening other than a door next to a control pad, and 45 seconds for a door next to a control pad. The system at the central monitoring location, (1) records the event, and (2) notifies a human
operator what’s happening within 30 seconds of receipt of the alarm sent from the local home monitoring system, and (3) automatically dial the home, within 45 seconds of receipt of the alarm sent from the local home monitoring system, and hands-off the call to the operator, who will to attempt to verify that there is a break-in. If no one answers, or someone answers but doesn’t give the agreed to safe-word or give the in-trouble word, then the operator will notify the police within 1 minute if no one answers, or 2 minutes if call is answered. All actions taken are recorded.
Part 1 (5 points): Create an architecture
Create an architecture for the whole system based on the patterns you choose in the last exercise. (Is you decide to change patterns, describe the changes including why.) Your description should include the following:
1. A diagram showing the Company’s Central Monitoring Center, and multi-homes being monitored.
2. A diagram of the architecture for the Central Monitoring Center.
3. A diagram of the architecture in a typical Home.
4. A short description of each software component.
Use the notation described in the SWAIP book for now.
Part 2 (5 points): Describe the qualities that are important for the system.
Apply the appropriate techniques from Chapter 14 (or in the pattern description, if any) to verify that you architecture is likely to produce a system that achieves the quality goals you identified in Assignment 4 (i.e., minimums & maximums) and satisfies any constraints in the customer description (this constrains are qualities that you must achieve). If you need certain values, e.g. execution speed of the CPU or how many cores in the CPU, then either do some research on reasonable values make a list of the values you obtain from your research or any assumptions you made and give a reference to the source.
If you determine that for some reason, your architecture does not achieve your quality goals, then explain why. (You may find that some goals are not achievable).
Create a PDF file with your results for part 1 & 2.
SAMPLE ANSWER
Software Architecture
Introduction
A home security alarm is a system designed to detect intrusion and/or unauthorized entry into a building or area. They are often used in residential and commercial properties for protection against property damage or burglary (theft). The most basic alarm consists of one or more sensors to detect intruders, and an alerting device to indicate the intrusion. However, a typical premises security alarm employs the following components: Premises control unit (PCU), or panel, Sensors, Alerting devices, Keypads, Interconnections and Security devices.
Architectural Structure
The architectural structure of the home alarm system design is shown in the block diagram below. The central system will handle all the sensors and keypad input, output information to LCD screen, indicate system status on LED, and make buzz or voice alarm.
Figure 1: Architectural Structure
Hardware & Software Tradeoffs
The IR motion sensor is quite inexpensive hence it should be bought for this design. It is also necessary to acquire one of the smoke detector from home to be used to sound the alarm in case of smoke detection. The architectural structure of our design is shown in the block diagram shown in figure 1 above. The central system will handle all the sensors and keypad input, output information to LCD screen, indicate system status on LED, and make buzz or voice alarm. Besides some necessary resistor and capacitor connections to the ISD1420 chip, the software makes the major part of the work mainly to ensure that home alarm system if fully customizable and consists of a lot of features. It need to monitors all the sensors, and time the appropriate seconds in order to play certain voice pattern (ex. “Temperature, smoke error, please…” “Door or window error, please…”) depending on which sensor goes wrong. It also needs to handle the user interface via keypad and LCD screen.
Program & Hardware Design
Program Detail
The timing is the hardest part of the program. This implies that when any sensor goes wrong, the program has to wait for a number of seconds as set by the user, and then make ISD1420 chip play back the necessary voice pattern as envisaged. The voice playback chip does not have a very fast internal clock, so the delay function has to be played manually in the program after setting the address bits, and then making the chip play. Besides, we also need to implement the keypad function so it acts accordingly when the LCD is displaying certain menu. In the system there are 12 submenus. For example, set temp defines the lowest temperature allowable prior to sounding the alarm (70~120F, with a 1F step size). The Sec. Allow is the time in second before the voice alarm goes off (0~30sec, with step size of 5 seconds). The submenus are shown in the table below:
| 1.Enable System
2.(*)Temp Sensor 3.(*)Mot. Sensor 4.(*)Smk. Sensor 5.(*)Mag. Switch 6.Set Temp: 100F |
7.(*)Voice Alarm
8.(*)Buzz Alarm 9.New Pswd: A. Buzz Freq: 7 B. Buzz Skim: 3 C. Sec. Allow: 10 |
There is also a simple de-bounce feature for the keypad, and it will sound a buzz when any key is pressed. Also the backspace feature is implemented so that when a wrong password is entered by the user, it is possible to use this key to delete the number entered previous previously. The password is masked on LCD for a safer purpose.
Hardware Detail
The first sensor we have is the temperature sensor. This is done using a digital thermometer utilizing the same circuit. This was achieved through incorporation of the National Semiconductor LM34 temperature sensor, together with National Semiconductor LMC7111 OpAmp chip for the amplification of the output voltage going into ADC. The final connection of our circuit looks like the following.
Figure 2: Main Connections
The second sensor is the motion sensor which has some IC components as well as a few NPN transistors in the circuit. The base pin together with ground are taken and connected to the ADC pin input, however, the alarm goes off when the voltage exceed VTH (threshold voltage). The other sensor is the smoke detector which is equipped with piezoelectric buzzer, which has F (feed back), M (metal plate) three pins, and C (main electrode). The piezoelectric buzzer consists of an internal crystal and it sounds the alarm if small current is applied (voltage drop).
The final sensor is the magnetic switches and it is normally closed meaning that when the switch is right next to each other, the resistance is zero. So the switch is driven with a 10K pull-up resistor, and connects the output to the ADC. A simple AND/OR gate was built by using 1 74LS00 chip since we have two magnetic switches.
Result of the Design
Speed of Execution
The speed of the execution is very well. At start the system boots up with default password 1234 allowing the user to navigate through menu, and enabling or disabling each type of sensor. If a particular sensor is enabled, the LCD screen will output a * symbol just immediately before the sensor name. Enable/disable voice, the alert temperature, or buzzer alarm can be set by the user, and even specify the ring tone and frequency of the buzzer alarm as well as the time needed prior to the voice alarm goes off. The button de-bounce scheme also works fine so users can navigate through the menu and use the keypad perfectly. This is highly essential because it usually bring with itself convenience to the user as well as enabling timely operation of the home alarm system while at the same time making sure that the system is easy to use. This is an essential feature for easy working or operation of the system which enables the highest level of the system operation at all times.
Accuracy
After the user enables the security system, the green status LED will lid to indicate the system status. User can now enter proper password to unlock the system. If any sensor goes wrong, the LCD will output ERROR and with proper initial for the sensor (T for temperature, M for motion, S for smoke, D for door or window magnetic switch). The red led light be will flashing at 4Hz to indicate such event. If the buzz alarm is enable, it will sound the tone that user choose. If the voice alarm is enabled, it will wait for few seconds (user specified), if the system is still not locked, then it will start playing voice to indicate which sensor goes wrong. (For example, “Temperature Error, please check and unlock the security system.”) If another sensor goes wrong after that, the system will also act accordingly and indicate that in the voice alert in addition to the LCD screen. (“Temperature Motion Error, please check and unlock the security system.”)
Safety
As soon as user enters the correct password, the system will be unlocked and the buzzer and voice playback will stop. The user can now navigate through our menu and make any changes in the settings.
Usability
The home alarm system is very practical. It can be used not only in the home environment but also in a business environment too and works by monitoring the surrounding for not only protection of property as well as lives. Besides, the system is also highly customizable for the purpose of suiting each one’s need and preference.
Expectation and Improvement
The result of the home alarm system design meets the expectation whereby every sensor is supposed to be working and will sound specific alarm when the system goes into alert status. The keypad and LCD also offer great interface and users can be familiar with the system in less than few seconds. The system also has 4 output patterns using all 8 pins. The designed home alarm system is envisaged to effectively work in order to prevent intrusion or property damage which can further be improved subsequently for better performance.
An architectural structure of the designed home alarm system is shown in the prototype shown in the diagrams shown below.
References
Trimmer, H. W. (1981). Understanding and Servicing Alarm Systems. Stoneham: Butterworth.
Walker, P. (1985). Electronic Security Systems. Cambridge, UK: University Press
Weber, T. L. (1985). Alarm Systems and Theft Protection (2nd ed.). Stoneham, MA: Butterworth.
We can write this or a similar paper for you! Simply fill the order form!




