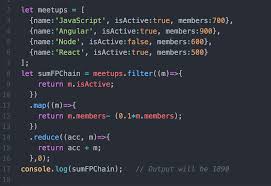
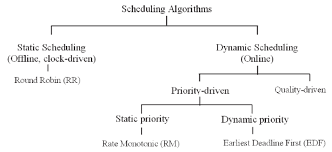
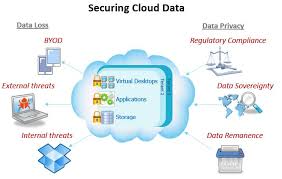
Web Assignment on Cyber Security and Crime Unit III Web Assignment
Web Assignment on Cyber Security and Crime Instructions
In this assignment, you will research and identify one of the laws that govern computer access and trespass. Begin by selecting ONE of the following governances, laws, or standards:

- The USA Patriot Act of 2001:
- http://www.justice.gov/archive/ll/highlights.htm
- The Computer Fraud and Abuse Act:
- http://www.pbs.org/wgbh/pages/frontline/shows/hackers/blame/crimelaws.html
- The Electronic Communications Privacy Act:
- https://it.ojp.gov/default.aspx?area=privacy&page=1285
- The Payment Card Industry Data Security Standard:
- https://www.pcisecuritystandards.org/security_standards/index.php
- Health Insurance Portability and Accountability Act:
- http://www.dol.gov/ebsa/publications/yhphipaa.html
- Another governance, law, or standard of your choosing.
After conducting research online, write a 500-word paper. Within the paper, including each of the following:
1 Provide an overview of the governance, law, or standard explaining how it is intended to protect civilians.
2 Does adhere to the governance, law, or standard includes any nuisances? Does it place a hardship on users or organizations? List them.
3 Describe an example scenario where the governance, law, or standard is violated (this can be real or fictitious).
4 Provide your own thoughts about the effectiveness of governance, law, or standard. Does it actually accomplish its intentions?
5 Two references (websites, the CSU Online Library, or books)