Logical Digit Signed Multiplier Project
Create a 4 bit Logical Digit Signed Multiplier Project with the following specifications:
INPUTS
A
4 bit 2’s complement binary number. This could be positive or negative.
B
4 bit 2’s complement binary number. This could be positive or negative.
OUTPUT: 8 bit 2’s complement binary number (This could be a positive or negative number)
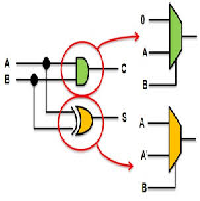
The overall circuit should look like this:
At a minimum, the circuit must be implemented using controlled inverters and an unsigned multiplier as discussed in class:
Logical Digit Signed Multiplier Project NOTES
1) The Controlled Inverters and Unsigned multiplier must be implemented as sub-circuits as demonstrated in class. These sub-circuits are used to build the 2’s Complement Signed Multiplier.
2) You are only allowed to use the basic gates: AND, OR, XOR, NOT.
3) You are NOT allowed to use Logisim’s built in circuits (i.e. Adders and Multiplexers). However, you are allowed to use the basic gates to build your own Adders and Multiplexers.
4) Once completed, please ZIP your CIRC file in the following format: CS212_Lastname_Firstname.zip.
Logical Digit Signed Multiplier Project overall circuit
The overall circuit should look like this:
At a minimum, the circuit must be implemented using controlled inverters and an unsigned multiplier as discussed in class:
NOTES
1) The
Logical Digit Signed Multiplier Project and Controlled Inverters and Unsigned multiplier
Controlled Inverters and Unsigned multiplier must be implemented as sub-circuits as demonstrated in class. Logical Digit Signed Multiplier Project These sub-circuits are used to build the 2’s Complement Signed Multiplier.
2) You are only allowed to use the basic gates: AND, OR, XOR, NOT.
3) You are NOT allowed to use Logisim’s built in circuits (i.e. Adders and Multiplexers). However, you are allowed to use the basic gates to build your own Adders and Multiplexers.